A vulnerability scanner is at the heart of a typical vulnerability management solution. It uses a list of known vulnerabilities to spot potential problems of the system. Traditionally, a vulnerability scanner either conducts dynamic penetration test or statically checking the version of examined software for a match in a vulnerability database. The more information the scanner has, the more accurate its performance.
Instead of conducting a penetration test or checking the version of binaries to find the known vulnerabilities, Dr. Binary took a different approach: A software vulnerability can be represented as one or several code fragments. Dr. Binary first extracts the vulnerable code fragments and generate "embeddings" as the vulnerability signature. Then given an input program, Dr. Binary decomposes it into code fragments, generate their embeddings, and then check these embeddings with the ones in the vulnerability database, to determine the presence of vulnerability.
In the following paragraphs, we use CVE-2017-0782 [1,2] as an example to illustrate how to use Dr. Binary to search vulnerabilities in binaries. It is an Android RCE vulnerability located in the bluetooth driver.
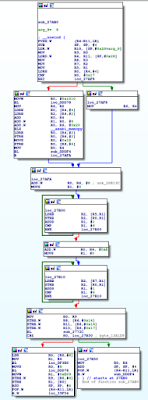 |
| Figure 1: CVE-2017-0782 Vulnerable Function |
1. Build Vulnerability Database
We first get the Bluetooth driver file (n5x_android70_nbd90w/bluetooth.default.so) [3] and locate the corresponding vulnerable function of CVE-2017-0782 as shown in Figure 1. The offset of this function in the binary is 0x27AB0. Now we add this vulnerability into the Dr. Binary's vulnerability database.
- Click "Vulnerabilities" and create one product named "Bluetooth" as shown in Figure 2.
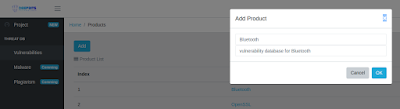 |
| Figure 2: Create Bluetooth Vulnerability Database |
- Add CVE-2017-0782 in the vulnerability database. The address is 0x27AB0 with the base address set to 0x00. The offset used in Dr. Binary means (virtual address - base address). The driver file(n5x_android70_nbd90w/bluetooth.default.so) should also be uploaded so that Dr. Binary can extract the vulnerable function from it. Then click "Add" to add CVE-2017-0782.
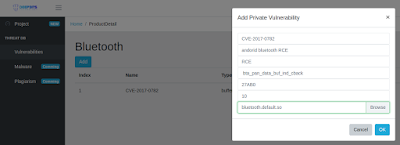 |
| Figure 3: Add Private Vulnerability CVE-2017-0782 |
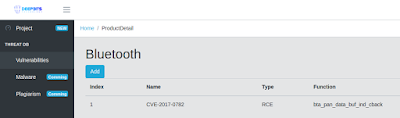 |
| Figure 4: Screenshot after CVE-2017-0782 is added |
2. Conduct the Scan
- Click projects on left aside menu and create a new project named Bluetooth
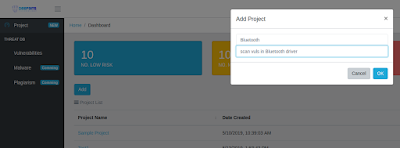 |
| Figure 5: Create a new project Bluetooth |
- Click the project you just created, and within the project, click "Add" to upload the file you want to scan (for instance, "s8_android70-rom/bluetooth.default.so").
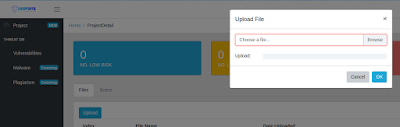 |
| Figure 6: Upload file |
- Create the scan, and in the popup windows, you can specify file and vulnerability you want to scan, click "OK".
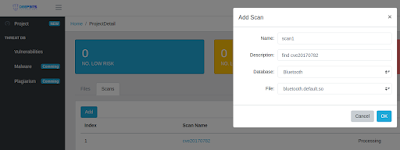 |
| Figure 7: Create a scan |
Now you can see a status update. Dr. Binary take the binary and running the analysis. It may take several minutes to get the results.
3. Analyze the result
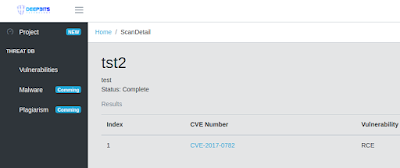 |
| Figure 8: Analysis results |
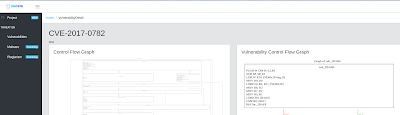 |
| Figure 9: CVE-2017-0782 |
Click the scan name, and enter the analysis results. Now you can see that Dr. Binary find a potential vulnerability CVE-2017-0782 in binary "s8_android70-rom/bluetooth.default.so". Click CVE-2017-0782 and then you see the details about the CVE-2017-0782. The right column displays the actual control flow graph of CVE-2017-0782 that Dr. Binary extracted from the vulnerability database you just created. The left column displays a list of functions' control flow graphs that are most similar to the vulnerability CVE-2017-0782. By comparing the CFGs, you can identify that the uploaded binary "s8_android70-rom/bluetooth.default.so" does have the vulnerability CVE-2017-0782.
Conclusion
From the above discussion, we can see that Dr. Binary can help vulnerability researchers to quickly search the binary code for known vulnerabilities. We will write more blogs to discuss various applications of Dr. Binary on different security problems.









No comments:
Post a Comment